Day 6: Decoding File Permissions: Harnessing Access Control Lists for Security Mastery
Table of contents
File Permissions
In Linux, file permissions determine who can do what with a file or directory. There are three main types of permissions:
Read: This permission allows you to view the contents of a file or directory.
Write: With this permission, you can modify the contents of a file or directory. You can also delete or rename it if it's a file, or add, remove, or rename files within a directory.
Execute: This permission is specifically for files, and it allows you to run the file as a program or script. For directories, it allows you to access files or subdirectories within that directory.
Permissions are set for three categories of users:
Owner: The user who created the file or directory.
Group: A collection of users who share certain permissions. Every file and directory has an associated group.
Others: All other users who are not the owner or part of the group.
Permissions are represented by a series of letters or symbols. For example, "r" stands for read permission, "w" for write permission, and "x" for execute permission. They are arranged in groups of three, one for each category of user (owner, group, others).
To see the permissions of a file or directory, you can use the ls -l command in the terminal. It will display something like this:
ls -l
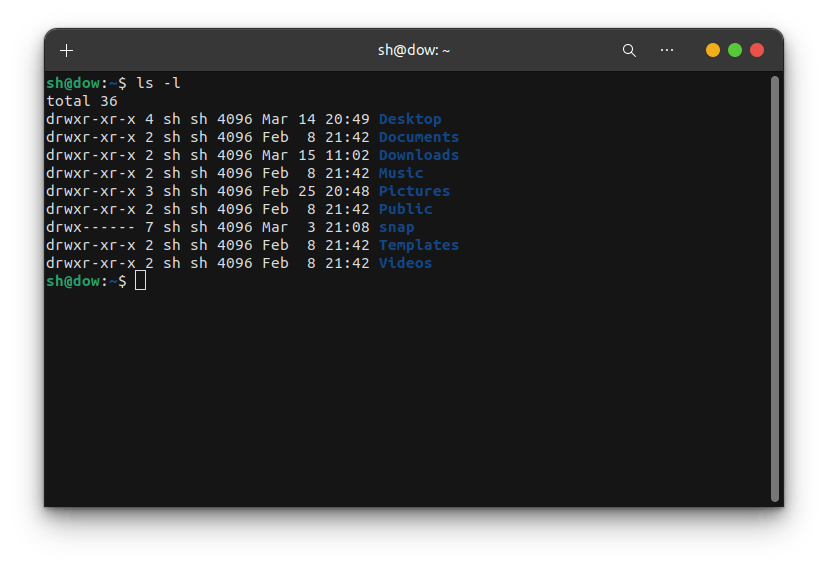
In this example, "rw-" means the owner has read and write permissions, while the group and others have only read permission.
To change permissions, you can use the chmod command followed by a series of letters or symbols representing the desired permissions. For example:
chmod u+x colors.txt
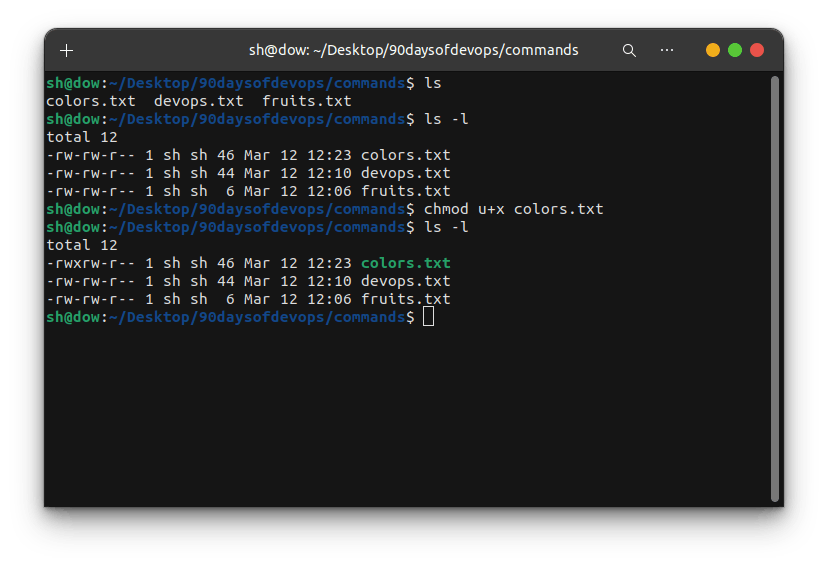
This command adds execute permission for the owner of the file colors.txt.
Each of the three permissions are assigned to three defined categories of users. The categories are:
owner — The owner of the file or application.
"chown" is used to change the ownership permission of a file or directory.
group — The group that owns the file or application.
"chgrp" is used to change the group permission of a file or directory.
others — All users with access to the system. (outised the users are in a group)
"chmod" is used to change the other users permissions of a file or directory.
Understanding and managing file permissions is crucial for maintaining security and controlling access to your files and directories in Linux.
Access Control Lists
Imagine you have a treasure chest (a file or folder) and you want to control who can open it and what they can do with what's inside. Regular permissions are like having a simple lock where you can give one key to someone (the owner), another key to a few people (the group), and anyone else (others) can't open it.
Now, Access Control Lists (ACLs) are like having a magical lock with a list of names and specific instructions for each person. With ACLs, you can say things like:
"Alice can open the chest and take anything."
"Bob can only look inside but can't take anything out."
"Charlie can't open the chest at all."
So, instead of just having one key for everyone, you can have a list of detailed permissions for each person. This gives you more control over who can access your treasure and what they can do with it.
Now, let's try out some commands to see how ACLs work in action:
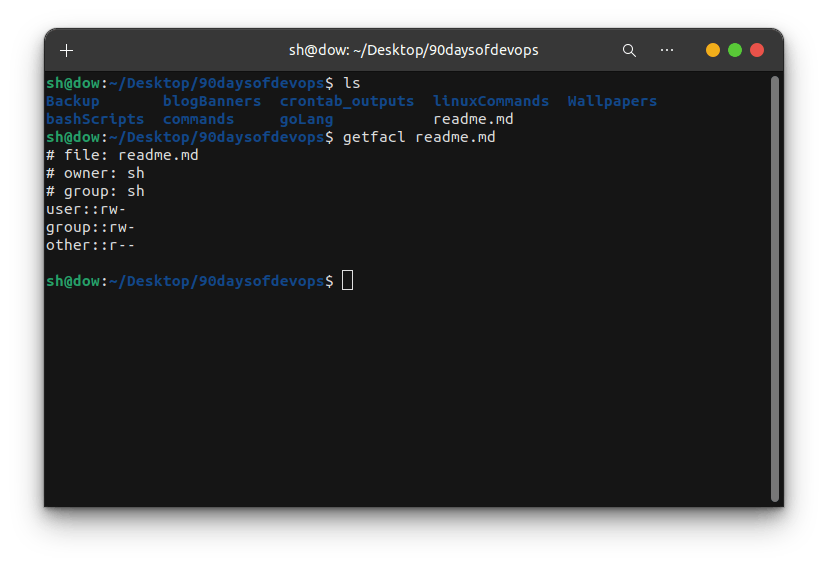
getfacl: This command lets you see the ACLs for a file or directory. It's like peeking into your magic spellbook to see who has what permissions.
getfacl filenameThis will show you a list of users and their permissions for the specified file.
setfacl: This command allows you to set or modify ACLs for a file or directory. It's like adding new spells to your magic spellbook.
setfacl -m u:alice:rw filenameThis command gives Alice read and write permissions to the specified file.
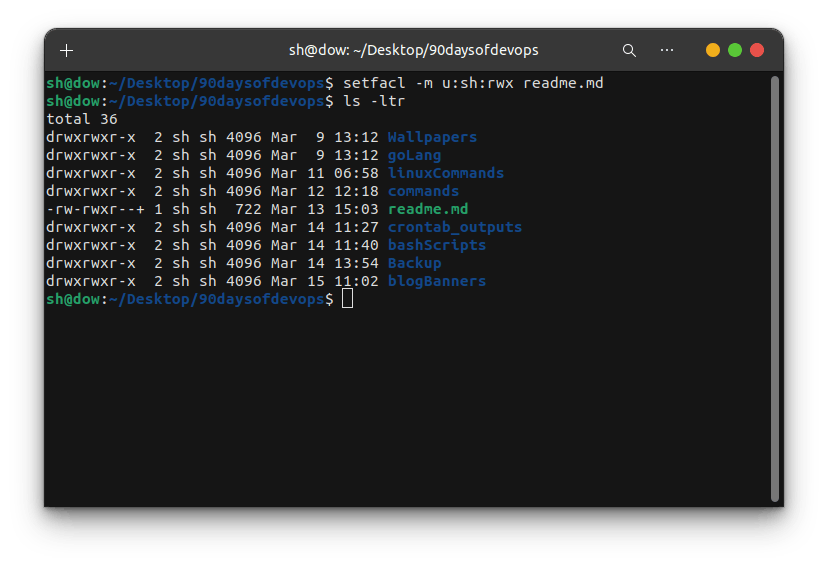
By using these commands, you can manage who has access to your files and what they're allowed to do with them. Just like having a magic spellbook to protect your treasures, ACLs give you fine-grained control over your data and who can access it.
"Fuel my passion and support my journey by clicking 'Buy me a coffee' today!"
~Dipen : )

